Are you looking for a Microsoft 70-410 exam questions? Are you looking for Microsoft 70-410 exam sample questions to identify gaps in your knowledge that may hurt you on the exam? GreatExam is your best choice! We are committed on providing you with the latest and most accurate 70-410 exam preparation material.
QUESTION 351
You work as an administrator at L2P.com. The L2P.com network consists of a single domain named L2P.com. All servers in the L2P.com domain, including domain controllers, have Windows Server 2012 R2 installed.
You have just executed the Uninstall-WindowsFeature Server-Gui-Shell L2P.com server, named L2P-SR13.
Which of the following is the reason for doing this?
A. To only remove Windows Explorer from L2P-SR13.
B. To only remove the Windows Internet Explorer from L2P-SR13.
C. To only remove the components and files related to Windows Explorer from L2PSR13.
D. To remove Windows Explorer, Windows Internet Explorer, and all associated components and files from L2P-SR13.
Answer: D
Explanation:
Minimal Server Interface
If the server has a full installation of Windows Server, and I need to bring the server down to minimal server interface, I only need to remove the Server-GUI-Shell. The command is shown here.
Get-WindowsFeature Server-Gui-Shell | Uninstall-WindowsFeature – restart
Minimal Server Interface is situated between the Server Core and Server with a GUI modes, you can either install features on Server Core or remove features from Server with a GUI to reach the Minimal Server Interface installation state
http://blogs.technet.com/b/heyscriptingguy/archive/2013/01/25/use-powershell-to-remove-the-gui-on-windows-server-2012.aspx
http://blogs.technet.com/b/server_core/archive/2012/05/09/configuring-the-minimal-server-interface.aspx
QUESTION 352
You work as an administrator at L2P.com. The L2P.com network consists of a single domain named L2P.com. All servers in the L2P.com domain, including domain controllers, have Windows Server 2012 R2 installed.
You have been instructed to add a new domain controller to L2P.com’s existing environment.
Which of the following actions should you take?
A. You should consider making use of Server Manager.
B. You should consider making use of Authorization Manager.
C. You should consider making use of Remote Desktop Gateway Manager.
D. You should consider making use of Network Load Balancing Manager.
Answer: A
Explanation:
http://social.technet.microsoft.com/wiki/contents/articles/12370.step-by-step-guide-for-setting-up-windows-server-2012-domain-controller.aspx
QUESTION 353
You work as an administrator at L2P.com. The L2P.com network consists of a single domain named L2P.com. All servers in the L2P.com domain, including domain controllers, have Windows Server 2012 installed.
You have been instructed to modify an Active Directory computer object.
Which of the following actions should you take?
A. You should consider making use of the Get-ADComputer Windows PowerShell cmdlet.
B. You should consider making use of the Set-ADComputer Windows PowerShell cmdlet
C. You should consider making use of the New-ADComputer Windows PowerShell cmdlet
D. You should consider making use of the Get-ADComputerServiceAccount Windows PowerShell cmdlet
Answer: B
Explanation:
Set-ADComputer – Modifies an Active Directory computer object.
http://technet.microsoft.com/en-us/library/ee617263.aspx
QUESTION 354
You work as an administrator at L2P.com. The L2P.com network consists of an Active Directory forest that contains a root domain, named L2P.com, and two child domains, named us.L2P.com and uk.L2P.com. All servers on the L2P.com network have Windows Server 2012 R2 installed.
The root domain hosts a domain local distribution group, named L2PGroup.
You are preparing to issue L2PGroup read-only access to a shared folder hosted by the us.L2P.com domain.
You want to make sure that L2PGroup is able to access the shared folder in the us.L2P.com domain.
Which of the following actions should you take?
A. You should consider re-configuring L2PGroup as a universal Admins group.
B. You should consider re-configuring L2PGroup as a universal security group.
C. You should consider re-configuring L2PGroup as a global administrators group.
D. You should consider re-configuring L2PGroup as a local administrators group.
Answer: B
Explanation:
Group scope Universal can be assigned permissions in any domain or forest.
http://technet.microsoft.com/en-us/library/cc781446(v=ws.10).aspx http://technet.microsoft.com/en-us/library/cc755692(v=ws.10).aspx
QUESTION 355
You work as an administrator at L2P.com. The L2P.com network consists of a single domain named L2P.com.
L2P.com has a domain controller, named L2P-DC01, which has Windows Server 2012 R2 installed. Another L2P.com domain controller, named L2P-DC02, has Windows Server 2008 R2 installed.
You have deployed a server, named L2P-SR15, on L2P.com’s perimeter network. L2PSR15 is running a Server Core Installation of Windows Server 2012 R2.
You have been instructed to make sure that L2P-SR15 is part of the L2P.com domain.
Which of the following actions should you take?
A. You should consider making use of Set-Computer Windows PowerShell cmdlet on L2P-SR15.
B. You should consider making use of Get-Computer Windows PowerShell cmdlet on L2P-SR15.
C. You should consider making use of Test-Computer Windows PowerShell cmdlet on L2P-SR15.
D. You should consider making use of Add-Computer Windows PowerShell cmdlet on L2P-SR15.
Answer: D
Explanation:
Add-Computer – Add the local computer to a domain or workgroup.
http://technet.microsoft.com/en-us/library/hh849798.aspx
QUESTION 356
You work as an administrator at L2P.com. The L2P.com network consists of two Active Directory forests, named L2P.com and test.com. There is no trust relationship configured between the forests.
A backup of Group Policy object (GPO) from the test.com domain is stored on a domain controller in the L2P.com domain. You are informed that a GPO must be created in the L2P.com domain, and must be based on the settings of the GPO in the test.com domain.
You start by creating the new GPO using the New-GPO Windows PowerShell cmdlet. You want to complete the task via a Windows PowerShell cmdlet.
Which of the following actions should you take?
A. You should consider making use of the Invoke-GPUpdate Windows PowerShell cmdlet.
B. You should consider making use of the Copy-GPO Windows PowerShell cmdlet.
C. You should consider making use of the New-GPLink Windows PowerShell cmdlet.
D. You should consider making use of the Import-GPO Windows PowerShell cmdlet.
Answer: D
Explanation:
Import-GPO -Imports the Group Policy settings from a backed-up GPO into a specified GPO.
http://technet.microsoft.com/en-us/library/ee461044.aspx
QUESTION 357
You work as an administrator at L2P.com. The L2P.com network consists of a single domain named L2P.com. All servers in the L2P.com domain, including domain controllers, have Windows Server 2012 R2 installed.
L2P.com has a server, named L2P-SR15, which is configured as a file server.
You have received instructions to make sure that a user, named Mia Hamm, has the ability to generate a complete backup of L2P-SR15 via Windows Server Backup.
Which of the following actions should you take?
A. You should consider making use of Computer Management to configure the local groups.
B. You should consider making use of Computer Management to configure the domain local groups.
C. You should consider making use of Computer Management to configure the global groups.
D. You should consider making use of Computer Management to configure the administrator groups.
Answer: A
Explanation:
To perform backups or recoveries by using Windows Server Backup, you must be a member of the Administrators or Backup Operators groups.
http://technet.microsoft.com/en-us/library/ee849849%28v=ws.10%29.aspx
Notes
You can only use Backup locally; you cannot backup a remote computer.
You can only back up and restore System State data on a local computer.
You cannot back up and restore System State data on a remote computer even if you are an administrator on the remote computer.
http://technet.microsoft.com/en-us/library/cc776822%28v=ws.10%29.aspx
QUESTION 358
You work as a senior administrator at L2P.com. The L2P.com network consists of a single domain named L2P.com. All servers on the L2P.com network have Windows Server 2012 R2 installed.
You are running a training exercise for junior administrators.
You are currently discussing the Windows Firewall with Advanced Security feature.
Which of the following is TRUE with regards to Windows Firewall with Advanced Security? (Choose all that apply.)
A. It provides host-based, two-way network traffic filtering for a computer.
B. It provides host-based, one-way network traffic filtering for a computer.
C. It blocks unauthorized network traffic flowing into or out of the local computer.
D. It only blocks unauthorized network traffic flowing into the local computer.
E. It only blocks unauthorized network traffic flowing out of the local computer.
Answer: AC
Explanation:
Windows Firewall with Advanced Security is an important part of a layered security model.
By providing host-based, two-way network traffic filtering for a computer, Windows Firewall with Advanced Security blocks unauthorized network traffic flowing into or out of the local computer. Windows Firewall with Advanced Security also works with Network Awareness so that it can apply security settings appropriate to the types of networks to which the computer is connected. Windows Firewall and Internet Protocol Security (IPsec) configuration settings are integrated into a single Microsoft Management Console (MMC) named portant part of your network’s
Windows Firewall with Advanced Security, so Windows Firewall is also an im isolation strategy.
http://technet.microsoft.com/en-us/library/hh831365.aspx
QUESTION 359
You work as a senior administrator at L2P.com. The L2P.com network consists of a single domain named L2P.com. All servers on the L2P.com network have Windows Server 2012 R2 installed.
You are running a training exercise for junior administrators.
You are currently discussing connection security rules.
Which of the following is TRUE with regards to connection security rules? (Choose all that apply.)
A. Connection security rules allows for traffic to be secured via IPsec.
B. Connection security rules do not allow the traffic through the firewall.
C. Connection security rules are applied to programs or services.
D. Connection security rules are applied between two computers.
Answer: ABD
Explanation:
Connection security involves the authentication of two computers before they begin communications and the securing of information sent between two computers. Windows Firewall with Advanced Security uses Internet Protocol security (IPsec) to achieve connection security by using key exchange, authentication, data integrity, and, optionally, data encryption.
How firewall rules and connection security rules are related
Firewall rules allow traffic through the firewall, but do not secure that traffic. To secure traffic with IPsec, you can create Computer Connection Security rules. However, the creation of a connection securityrule does not allow the traffic through the firewall. You must create a firewall rule to do this, if the traffic is not allowed by the default behavior of the firewall. Connection security rules are not applied toprograms or services; they are applied between the computers that make up the two endpoints.
http://technet.microsoft.com/en-us/library/cc772017.aspx
http://technet.microsoft.com/en-us/library/cc772017%28v=ws.10%29.aspx
QUESTION 360
You work as an administrator at L2P.com. The L2P.com network consists of a single domain named L2P.com. All servers in the L2P.com domain, including domain controllers, have Windows Server 2012 R2 installed.
You have been instructed to make sure that L2P.com users are not able to install a Windows Store application. You then create a rule for packaged apps.
Which of the following is the rule based on? (Choose all that apply.)
A. The publisher of the package.
B. The publisher of the application.
C. The name of the package
D. The name of the application
E. The package version.
F. The application version.
Answer: ACE
Explanation:
Packaged apps (also known as Windows 8 apps) are new to Windows Server 2012 R2 and Windows 8.
They are based on the new app model that ensures that all the files within an app package share the same identity. Therefore, it is possible to control the entire application using a single AppLocker rule as opposed to the non-packaged apps where each file within the app could have a unique identity. Windows does not support unsigned packaged apps which implies all packaged apps must be signed.
AppLocker supports only publisher rules for Packaged apps.
A publisher rule for a Packaged app is based on the following information:
Publisher of the package
Package name
Package version
All the files within a package as well as the package installer share these attributes. Therefore, an AppLocker rule for a Packaged app controls both the installation as well as the running of the app. Otherwise, the publisher rules for Packaged apps are no different than the rest of the rule collections; they support exceptions, can be increased or decreased in scope, and can be assigned to users and groups.
http://technet.microsoft.com/en-us/library/hh994588.aspx
QUESTION 361
You work as a senior administrator at L2P.com. The L2P.com network consists of a single domain named L2P.com. All servers on the L2P.com network have Windows Server 2012 R2 installed.
You are running a training exercise for junior administrators.
You are currently discussing Group Policy preference.
Which of the following is TRUE with regards to Group Policy preference?
A. It supports applications and operating system features that are not compatible with Group Policy
B. It does not support item-level targeting.
C. It is the same as Group Policy filtering.
D. It does not cause the application or operating system feature to disable the user interface for the settings they configure.
Answer: AD
QUESTION 362
You work as an administrator at ABC.com. The ABC.com network consists of a single domain named ABC.com. All servers in the ABC.com domain, including domain controllers, have Windows Server 2012 R2 installed.
ABC.com has a domain controller, named ABC-DC01, which contains the ABC.com domain’s primary DNS zone. ABC.com’s workstations refer to ABC-DC01 as their primary DNS server.
You have been instructed to make sure that any DNS requests that are not for the ABC.com domain, is resolved by ABC-DC01 querying the DNS server of ABC.com’s Internet Service Provider (ISP).
Which of the following actions should you take?
A. You should consider configuring a reverse lookup zone.
B. You should consider configuring forward lookup zone.
C. You should consider configuring Forwarders.
D. You should consider configuring 019 IP Layer Forwarding.
Answer: C
Explanation:
A forwarder is a Domain Name System (DNS) server on a network that forwards DNS queries for external DNS names to DNS servers outside that network. You can also forward queries according to specific domain names using conditional forwarders.
You designate a DNS server on a network as a forwarder by configuring the other DNS servers in the network to forward the queries that they cannot resolve locally to that DNS server. By using a forwarder, you can manage name resolution for names outside your network, such as names on the Internet, and improve the efficiency of name resolution for the computers in your network.
http://technet.microsoft.com/en-us/library/cc754931.aspx
http://technet.microsoft.com/en-us/library/cc730756.aspx
QUESTION 363
You work as an administrator at L2P.com. The L2P.com network consists of a single domain named L2P.com. All servers on the L2P.com network have Windows Server 2012 R2 installed.
L2P.com has a server, named L2P-SR13, which is configured as the primary DNS server in the L2P.com domain. L2P.com has another server, named L2P-SR14, which makes use of L2PSR13 for DNS queries.
You want to make sure that running nslookup.exe from L2P-SR14 produces a result that shows the proper name of the default server.
Which of the following actions should you take?
A. You should consider creating a reverse lookup zone on L2P-SR14.
B. You should consider creating a forward lookup zone on L2P-SR14.
C. You should consider creating a reverse lookup zone on L2P-SR13.
D. You should consider creating a forward lookup zone on L2P-SR13.
Answer: C
Explanation:
When you start Nslookup from a command line, the following error message may be displayed: DNS request timed out
timeout was x seconds
Can’t find server name for address xxx.xxx.xxx.xxx: Timed out
Default servers are not available
Default Server: UnKnown
Address: xxx.xxx.xxx.xxx
where xxx.xxx.xxx.xxx is the Internet Protocol (IP) address of the host on which you are attempting to start Nslookup.
CAUSE When Nslookup starts, it attempts to resolve the IP address of its host’s DNS server to its fully qualified domain name (FQDN). If the DNS server does not respond or if the DNS server’s reverse lookup zones do not contain a PTR record for the DNS server’s IP address, the error message is displayed.
http://support.microsoft.com/kb/242906/en-us
QUESTION 364
You work as an administrator at L2P.com. The L2P.com network consists of a single domain named L2P.com. All servers on the L2P.com network have Windows Server 2012 R2 installed.
L2P.com has a server, named L2P-SR07, which has the ADDS, DHCP, and DNS server roles installed. L2P.com also has a server, named L2P-SR08, which has the DHCP, and Remote Access server roles installed. You have configured a server, which has the File and Storage Services server role installed, to automatically acquire an IP address. The server is named L2PSR09.
You then create reservation on L2P-SR07, and a filter on L2P-SR08.
Which of the following is a reason for this configuration?
A. It allows L2P-SR09 to acquire a constant IP address from L2P-SR08 only.
B. It configures L2P-SR09 with a static IP address.
C. It allows L2P-SR09 to acquire a constant IP address from L2P-SR07 and L2PSR08.
D. It allows L2P-SR09 to acquire a constant IP address from L2P-SR07 only.
Answer: D
Explanation:
To configure the Deny filter
In the DHCP console tree of DHCP Server 1, under IPv4, click Filters, right-click Deny under Filters, and then click New Filter. In the New Deny Filter dialog box, in MAC Address, enter a six hexadecimal number representing the MAC or physical address of DHCP Client 2, click Add, and then click Close. Under Filters right-click the Deny node, and then click the Enable pop-up menu item.
http://technet.microsoft.com/en-us/library/ee405265%28WS.10%29.aspx
QUESTION 365
You work as an administrator at L2P.com. The L2P.com network consists of a single domain named L2P.com.
L2P.com has a server, named L2P-SR15, which has Windows Server 2012 R2 installed. L2P.com also has a server, named L2P-SR16, which has Windows Server 2008 R2 SP1 installed.
You have been instructed to make sure that L2P-SR16 is able to run Windows PowerShell 3.0.
Which of the following actions should you take? (Choose two.)
A. You should consider making sure that L2P-SR16 has a full installation of Microsoft .NET Framework 4 installed.
B. You should consider making sure that L2P-SR16 has a full installation of Microsoft .NET Framework 2 installed.
C. You should consider making sure that L2P-SR16 has WS-Management 3.0 installed.
D. You should consider making sure that L2P-SR16 is upgraded to Windows Server 2012 R2.
Answer: AC
Explanation:
WS-Management 3.0 – Windows Management Framework 3.0 Includes Windows PowerShell 3.0, WMI, WinRM, Management OData IIS Extension, and Server Manager CIM Provider
Windows Management Framework 3.0 requires Microsoft .NET Framework 4.0.
http://www.microsoft.com/en-us/download/details.aspx?id=34595
QUESTION 366
You work as an administrator at L2P.com. The L2P.com network consists of a single domain named L2P.com. All servers on the L2P.com network have Windows Server 2012 R2 installed.
L2P.com has a server, named L2P-SR13. L2P-SR13 hosts a shared folder, named L2PShare, which has been shared as L2PShare$.
Which of the following is TRUE with regards to sharing the folder in this manner?
A. It allows all users to view L2PShare when browsing the network.
B. It prevents users from viewing L2PShare when browsing the network.
C. It only allows L2P-SR13’s users to view L2PShare.
D. It removes the permissions configured for L2PShare.
Answer: B
Explanation:
A hidden share is identified by a dollar sign ($) at the end of the share nameHidden shares are not listed when you look through the shares on a computer or use the “net view” command
Why Use Hidden Shares?
Using hidden shares on your network is useful if you do not want a shared folder or drive on the network to be easily accessible. Hidden shares can add another layer of protection for shared files against unauthorized people connecting to your network. Using hidden shares helps eliminate the chance for people to guess your password (or be logged into an authorized Windows account) and then receive access to the shared resource.
http://support.microsoft.com/kb/314984
http://technet.microsoft.com/en-us/library/cc784710(v=ws.10).aspx
QUESTION 367
You work as a senior administrator at L2P.com. The L2P.com network consists of a single domain named L2P.com. All servers on the L2P.com network have Windows Server 2012 R2 installed.
You are running a training exercise for junior administrators.
You are currently discussing printer pooling.
Which of the following is TRUE with regards to printer pooling? (Choose all that apply.)
A. Printers in a pool must be of the same model, and use the same printer driver.
B. Each printer in the pool must have a different printer driver.
C. Printer ports used in the pool must be of the same type.
D. The types of printer ports used in the pool must be mixed.
E. Pooled printers appear to workstations as a single printer.
F. A minimum of three printers are required to configure a printer pool.
Answer: AE
Explanation:
You can create a printing pool to automatically distribute print jobs to the next available printer. A printing pool is one logical printer connected to multiple printers through multiple ports of the print server. The printer that is idle receives the next document sent to the logical printer. This is useful in a network with a high volume of printing because it decreases the time users wait for their documents. A printing pool also simplifies administration because multiple printers can be managed from the samelogical printer on a server.
http://technet.microsoft.com/en-us/library/cc757086%28v=ws.10%29.aspx
QUESTION 368
You work as an administrator at ABC.com. The ABC.com network consists of a single domain named ABC.com. All servers in the ABC.com domain, including domain controllers, have Windows Server 2012 R2 installed.
You have installed the DNS Server Role on a ABC.com server, named ABC-SR13.
ABC.com’s workstations make use of a web proxy to access the Internet, and refer to ABC-SR13 as a primary DNS server.
You have been instructed to make sure that Internet host names for ABC.com’s workstations are not resolved by ABC-SR13.
Which of the following actions should you take?
A. You should consider configuring a primary zone on ABC-SR13.
B. You should consider configuring a secondary zone on ABC-SR13.
C. You should consider configuring a reverse lookup zone on ABC-SR13.
D. You should consider configuring a forward lookup zone on ABC-SR13.
Answer: A
Explanation:
Open DNS Server Manager | Expand DNS Server | Expand Forward Lookup Zones | Right Click on Forward Lookup Zones and select New Zone | Primary Zone | Zone Name: “.” (only dot, without quotation marks) When you create such a zone, you are configuring the DNS server to be the ultimate authority for the DNS namespace. The DNS server will no longer attempt to forward any DNS requests that it is not authoritative for.
When you install DNS on a Windows server that does not have a connection to the Internet, the zone for the domain is created and a root zone, also known as a dot zone, is also created. This root zone may prevent access to the Internet for DNS and for clients of the DNS. If there is a root zone, there are no other zones other than those that are listed with DNS, and you cannot configure forwarders or roothint servers.
Root domain This is the top of the tree, representing an unnamed level; it is sometimes shown as two empty quotation marks (“”), indicating a null value. When used in a DNS domain name, it is stated by a trailing period (.) to designate that the name is located at the root or highest level of the domain hierarchy. In this instance, the DNS domain name is considered to be complete and points to an exact location in the tree of names. Names stated this way are called fully qualified domain names (FQDNs).
http://technet.microsoft.com/en-us/library/cc772774%28v=ws.10%29.aspx http://youtu.be/KjMDtlR6Mhk http://support.microsoft.com/kb/298148/en-us
http://www.wincert.net/tips/windows-server/2510-how-to-remove-root-hints-in-windows-server-2008-r2-dns-server http://support.microsoft.com/kb/298148/en-us
QUESTION 369
You run a Windows Server 2012 R2, what is the PowerShell command to set preferred dns server. Note: Other config such as ip address should not be changed.
A. Register-DnsClient
B. Set-DnsClient
C. Set-DnsPreferredClientServerAddress
D. Set-DnsClientServerAddress
Answer: D
Explanation:
Set-DnsClientServerAddress – Sets DNS server addresses associated with the TCP/IP properties on an interface.
Set-DnsClientServerAddress -InterfaceIndex 12 -ServerAddresses (“10.0.0.1”)
There is a fair bit of confusion around the purpose of the Alternate DNS Server. This Post should hopefully put these questions to bed.
The general assumption is that, the Windows DNS Client on all counts, will send a DNS query to the Preferred DNS first. If this query fails, then it will query the Alternate DNS Server, and so on and so forth.
The above statement is true, however there is a twist.
The Windows DNS Client will reset the DNS Server Priority at periodic intervals. By default, the server priorities are reset every 15 minutes.
Let’s look at an example:
I have a DNS Client configured as follows:
Preferred DNS: 192.168.0.1
Alternate DNS: 10.10.0.1
The DNS Client will start by sending queries to 192.168.0.1. After 15 minutes it will switch priority to 10.10.0.1. Thus all queries will first be sent to 10.10.0.1 for a period of 15 minutes before switching back to 192.168.0.1
There is another condition that triggers a Priority Switch.
If say the Preferred DNS timed out on a DNS query, the DNS Client will send that DNS Query to the Alternate DNS.
If the Alternate DNS resolves the Query, the Priority will now switch to the Alternate DNS, until either it times out on a Query or the Priority Time Limit expires.
It is a common practice to configure the Preferred DNS Server with the IP of a Local Site DNS Server and the Alternate DNS Server with that of a Remote Site. The problem arises when Firewall/Network folk raise complaints that Clients are sending DNS Traffic to Remote DNS Servers. Well, that is because they have been configured to do so.
http://blogs.technet.com/b/ajayr/archive/2011/12/14/who-does-dns-client-prefer-preferred-or-alternate.aspx
http://technet.microsoft.com/en-us/library/cc738344%28v=ws.10%29.aspx http://technet.microsoft.com/en-us/library/jj590768.aspx
QUESTION 370
Command to set configure network interface primary dns server. Note: Other config such as ip address should not be changed.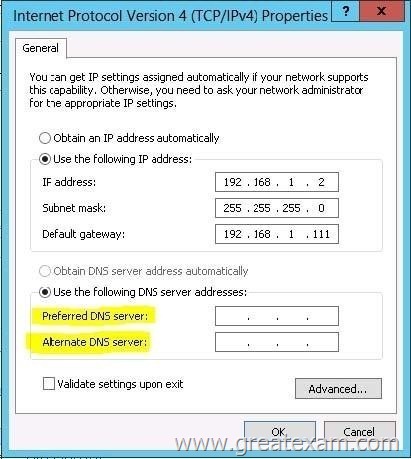
A. set-ipaddress
B. netsh
C. ipconfig
D. winipconfig
Answer: B
Explanation:
netsh interface ipv4 set dns name=”Local Area Connection” source=static address
=192.168.100.49 primary
http://exchangeserverpro.com/how-to-add-multiple-dns-servers-to-windows-server-2008-core/
Our 70-410 dumps are rich in variety. We offer 70-410 PDF dumps, 70-410 practice test and 70-410 VCE dumps. We ensure you can pass the 70-410 easily. Welcome to GreatExam.com.
Comments are closed.